Michael Gagnon
Who has not heard that “Knowledge is Power” in today’s technology connected economy? Knowing what to know is important but knowing what you don’t know is even more critical to execution. With so much information flowing in today’s marketplaces, how is information: and in particular, mobile information, made actionable on your employees favorite mobile device?
The ability for business to disrupt & win is directly related to the quality of relationships between an Enterprise & its customers, its employees, its partner/supplier ecosystem. Nurturing these relationships with free flowing, frictionless & ultimately secure mobile data is at the core of increasing the ecosystem effectiveness. Matching “Know How” with “Know Who” across the enterprise ecosystem is one of the incredible opportunities that data and mobility can harvest.
Technological innovation is so often cited as the fuel of disruption & transformation in the Enterprise. The reality is the more subtle. Intricate shifts in the relationship structures between customers, employees and partners/suppliers are what make the end game of ecosystem transformation possible. And secure mobility is a key catalyst.
But how do you get the information your customers, employees, partners/suppliers need need; when they need it and where they need it, in a simple, consumable and action oriented form on their favorite mobile device?
Bottom line is that knowledge is truly powerless unless and until it flows freely, transparently & with complete security to mobile users…. at point of need. Your ecosystem wants to execute work jobs where they can best happen and this is generally not at a desk as we are so often told by our customers.
Big Data systems are a great example of this conundrum. Big Data systems drive real time analytical capabilities provide a treasure trove of highly contextual, relevant information; derived from some of the most sensitive & proprietary subsets of data in the Enterprise. Big Data is at the core of new competitive capabilities in the Enterprise but does it suffer from mobile security bottlenecks as it tries to deliver insight from Hadoop Clusters to mobile devices?
How you get this information from your Hadoop Data Lake to your mobile device simply, securely & at scale, so users across your entire ecosystem can interact with complete trust and integrity? All of the work to create the situational context that is Big Data is worthless if it cannot be delivered in a totally transparent but totally simplified & secure manner to customers, employees partners & suppliers.
How to enable simplified, “intelligence grade” security at scale is the problem to the answer. Big Data systems need to fulfill their promise to mobile users in the same way they do for those same users fixed devices like PC’s. Could it be that traditional approaches to mobile security found in EMM systems now create too much complexity, cost & friction for the dynamic world of real time Big Data systems?
What if the networks that connect Big Data systems to mobile devices were inherently “intelligence grade” in terms of security transmission, delivery & data protection?
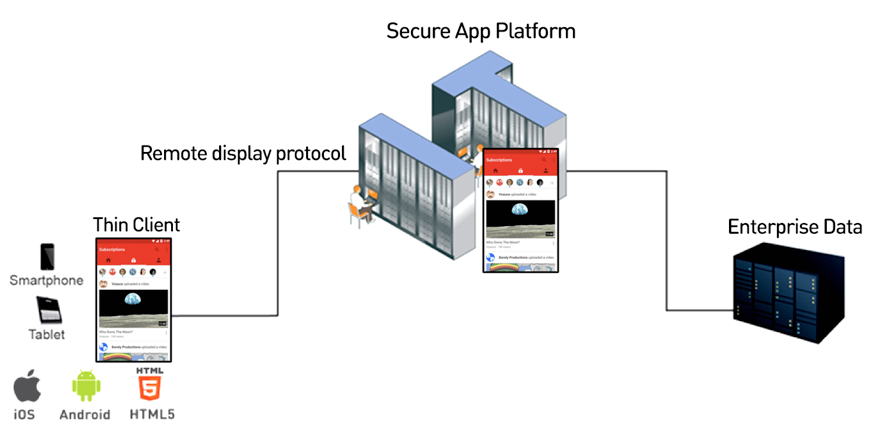
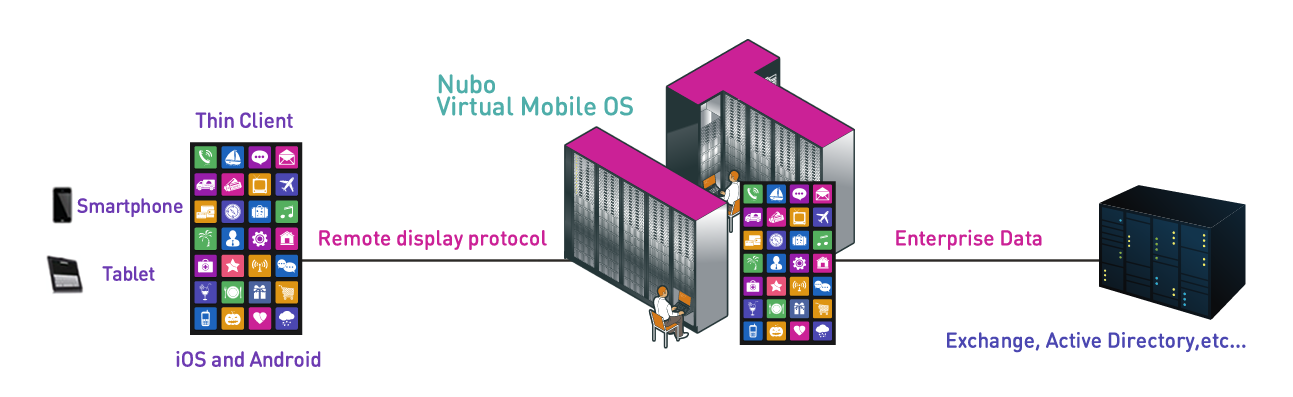
NUBO’s Virtual Mobile Infrastructure (VMI), provides a next generation approach to providing free flowing, transparent & secure delivery of information from Big Data & Cloud Systems to iOS & Android devices. Nubo VMI runs virtual Android mobile devices in a secure AWS Cloud or Premise based platform. Mobile apps are delivered via Nubo’s intelligent remote display protocol called UX over IP to customers, employees, partners/suppliers mobile devices.
The contribution that UX over IP makes to Enterprise security & ecosystem productivity is that Nubo VMI requires “zero data” in transit or on the device to operate ecosystem mobile apps normally. Mobile threat perimeters are reduced to zero with no compromise in user interaction & experience with mobile applications like Outlook & Office 365. With Nubo VMI there is simply no data to hack because there is no data on the mobile device to be hacked. You cannot steal what you cannot see.
Mobile app developers can radically reduce investments into the myriad of traditional mobile app security practices such as app vulnerability testing, mobile device compatibility testing, OS vulnerability testing & app wrapping to name just three. Nubo VMI will reduce mobile app development life cycles by 50% while reducing app development costs by 65% while increasing mobile app security to “intelligence grade”.
Nubo VMI is a platform that delivers radically simplified enablement of mobile apps for customers, employees, partners & suppliers across the Enterprise ecosystem. Using Nubo VMI, the right information is delivered to the right person at the right time where the work actually gets done. Enterprises can be incredibly flexible in the specific situational information that is delivered to users in their ecosystem without the traditional concerns, costs & complexities that are mobile app development as we know it today.
Relationships in the ecosystem will be enriched and empowered because of the incredible relevancy of information that can now be more safely delivered to mobile devices. Nubo VMI helps drive better customer experience ideation, ecosystem collaboration while taking cost, complexity and delays out of traditional mobile application dev-ops.
Winning in today’s market, demands that mobile ecosystem players be on the same page and at the same table with the right information for each and every user to leverage appropriately.