A lot has already been said about the WannaCry mega cyber-attack. Even if the first wave has already stopped, thanks to an effective kill switch, new waves are emerging, as some clones of this vicious virus are appearing. Thus, we should start learning about this cyber-attack and draw important conclusions to help us prepare for the future.
Some known (and unknown) facts about WannaCry:
- WannaCry took advantage of an already-known vulnerability (not a zero-day vulnerability) but was still able to spread all over un-patched computers. Effective patch management procedures implemented by organizations, could have prevented this kind of catastrophe. Still many large organizations have failed to do so.
- WannaCry exploits vulnerability through a well-known and used network service (SMB in Windows machines). Companies have thousands of different network services available. All of them potentially have network vulnerabilities that will be exposed in the future, thus being exploited for future attacks.
- So far, no one knows exactly how the malware is spread. There have been some rumors that it is spread through emails, but no one could confirm that. It could have been spread through other forms, such as mobile devices connected to company Wi-Fi or VPN.
When trying to predict the future of cyber-attacks, I could not avoid thinking how mobile devices would play an integral part of the next mega attacks, simply because of the following:
- The spread of mobile devices is huge. There are billions of mobile devices around the world . Each mobile device is now a smartphone, which means that it is actually a computer that has the same kind of vulnerabilities, just like the computers that were infected by WannaCry. Those mobile devices are everywhere, both physically and virtually, which means that they are connected to every network possible.
- Patch management is ineffective in mobile devices. Companies cannot simply use a patch management solution and make sure all their smartphones are patched. Smartphones, unlike desktops and laptops, are often owned by employees, and the company cannot install patches on them. Even if enterprises hope that the users install patches, as soon as they become available, this will not solve the problem, since in the mobile world, many devices are left without any effective patches.
- The protection on mobile devices nowadays is very poor. Companies believe that encrypting the data in the device (using a container) or in transit (using a VPN) serves as good protection. However, this will not stop a future cyber-attack such as WannaCry.
The only effective protection measure against such WannaCry-like mobile attacks will be a total separation between mobile devices and your data. The technology that has been proven to do such separation is Virtual Mobile Infrastructure (VMI). This is because of the nature of the solution, which does not just separate the data and the apps from the device, but also separates the network services. In VMI, all the connection from mobile devices are carried through a single remote display protocol, and there is no connection to any other (possibly vulnerable) network services.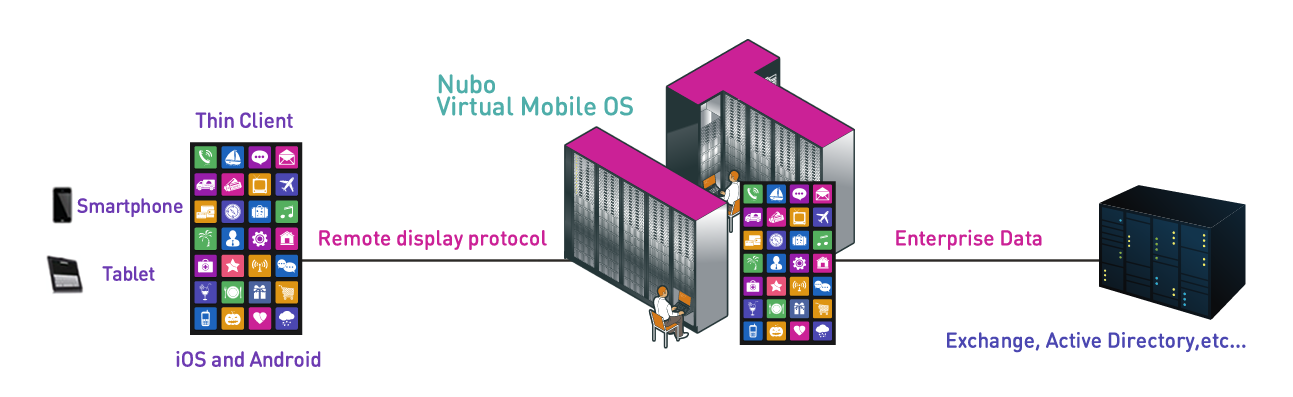
On a personal note, I believe that the next mega cyber-attack on smartphones is just around the corner; yet, I’m convinced that organizations can protect themselves by utilizing VMI, as the most effective mobile access solution.










