- All
- Blog
- Mobile
- Security
- Technology
- Uncategorized
Are you struggling to keep your remote team on track? Follow these 10 essential tips to maximize productivity, foster teamwork, and achieve success.
After a sudden surge of remote work during the pandemic, there was a significant decline. What does the future of remote work hold? Will it stay?
Powerful security techniques to better secure your applications and datacenter.
![]()
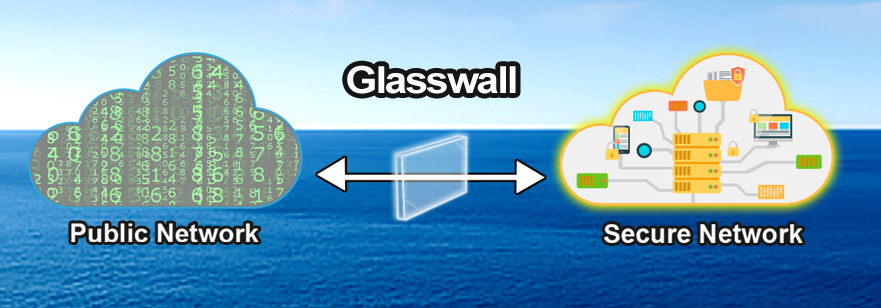
Glasswall Protection allows organizations to add apps and access data, while reducing the attack surface.
![]()
How secure mobile programs should look like for the most secure organizations?
![]()
Virtual mobile app platforms help gain control and security, even when IT seems to lose it.
![]()
WannaCry analysis concludes that your smartphone is probably the next one to be exploited…..
![]()
![]()
Mobile knowledge is power for sure, but is your current security approach hampering how your people & partners collaborate with your customers?
![]()
![]()