It is well known that every organization must provide some kind of mobility support. This applies to all enterprises, let alone financial services firms, hospitals, and even defense agencies. Moreover, organizations today are exposed to a wide range of threats and securing mobile systems has become a must. The level of security required is of course different from one organization to another, and depends on factors like: threat level, risk involved and others.
It’s obvious that the highest level of security needs to be enforced in military and such related industries. In this article, I would like to outline how secure mobile programs should look like for the most secure organizations. If you work for such an organization, you will immediately relate to the content below, but if you work at a less secure industry and/or organization, stay close since you will learn how to apply some essential security measures to your mobility program.
Main considerations to be addressed when planning the system
- End to End Protection – Consider all the different components in the system. The attacker is likely to attack the least protected component, just like the wolf attacks the weakest sheep in the herd.
- Threat Types – Make a list of all potential threats and prioritize them according to their severity. Be as thorough as possible, since most security precautions are directly tied to the specific threat they are supposed to handle.
- User Experience – Since security measures often compromise user experience, bear in mind that maintaining proper UX is necessary, when users use the system for their ongoing work.
Security system – Ground rules
Based on the threats at hand, start outlining some ground rules.
Here are some rules to be applied in the toughest of`environments:
- Protect the Mobile Devices – In mobility systems, the weakest and least secure component in organizations is usually mobile devices. There are thousands of them wandering around and they can be easily breached by a countless number of external sources.
- Zero Data on the Device – Sharing a huge amount of data on a large number of mobile devices make it almost impossible to track and detect data breaches. It is better to operate with a system that actually stores no data on the devices.
- Protect the Data Center –Many organizations think about device protection, while overlooking the data center. However, data center breaches can be much more dangerous. When an attacker enters the data center, he gains access to all the data in the
organization and what can happen then is all up to him. Think about risks such as a critical system suddenly shutting down at an airport or a big financial institution. Even the sky is not the limit when hackers penetrate enterprises’ data centers.
- Apps Pose risks – People easily understand the risks on hardware and network connections. However, the main risks are usually found at the software level. This is simply because software code is so huge that it’s fundamentally impossible to make sure all the apps in the organization are secure.
Detailing security measures by component
Now, let’s see how high security systems really look like and group the security measures by component:
The mobile device:
- Secure the operation system and hardware to make sure unauthorized malware/people do not damage the software modules.
- Remove unnecessary network components. Today, each smart phone has many different network components, such as Bluetooth, Wi-Fi, cellular, NFC, USB and more. Each network connection poses a potential risk, so it is better to remove unneeded components.
- Have a centralized encryption component in place, to make sure all apps use one safe encryption and no un-encrypted data is going out of the device.
- Install only apps that store zero data on the device and had been previously tested using penetration tests. Bear in mind that each new app version needs to be retested.
- Make sure all admins know exactly where all the devices are located (i.e. Mobile Device Management).
The network
- Military graded networks are not connected to the Internet, but use private closed networks that only pre-approved devices can connect to. This can be done by having an organization build its own private network, or by buying a virtual-private network
from a carrier.
- The network itself needs to be fully encrypted and not allow regular traffic to go through.
- Advanced firewall that does IP inspections of the app protocols, as well as strict filtering should be put in place.
The data center
- Sandboxes – Datacenters usually provide several types of services. Each service needs to be separated from the other services, so that if one service is compromised, it will not affect the other ones.
- Split services to frontend and backend – Each service should be separated to both frontend and backend service. In that case, if a frontend service with a direct connection to the device gets compromised, the main service data remains safe.
- Strict input validation – Each component needs to strictly validate its input parameters to make sure no one is trying to insert data into the service.
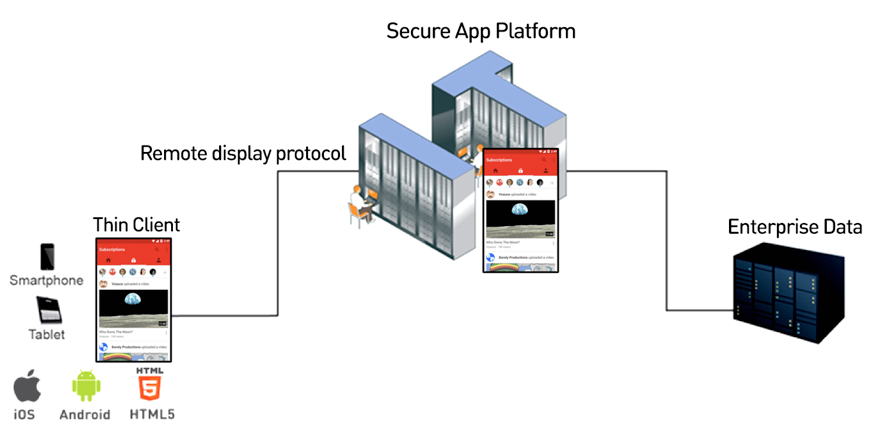
Virtual Mobile Infrastructure
With all such complicated security systems in place, there is only one technology that really does
the job faster and much simpler – Virtual Mobile Infrastructure (VMI).
VMI actually:
- Allows zero data to be stored on any app.
- Displays only one major app on the device (i.e. the thin client), which makes it easy to test the app.
- Uses one encryption protocol for all apps.
- Provides an additional separation in the data center since the secure VMI platforms actually separate between the devices and the apps, and the datacenter.
As this article draws on the most severe situations, which hopefully your organization will never need to experience, you can still implement some of the guidelines mentioned above, and get prepared for the security level your organization requires.