Taking in the security buffet that is the RSA Conference is a real eye-opening experience into the tremendous effort and resources that is put into securing the technologies we need to move forward as businesses and customers.
At the Nubo exhibit, we’ve been listening to many stories from security and mobility professionals at different levels about their sore spot – the Achilles’ heel if you will, of their enterprise data security and how this limits their ability to move forward with their greater enterprise strategy. But there’s been a running theme that ties these weak points together, and it’s very much a four-letter word to CISO’s, CIO’s, and IT professionals. You guessed it: B-Y-O-D.
While most enterprises have already accepted BYOD as a necessity for their future growth, most are far from comfortable with how well-positioned they are to deal with the plethora of vulnerabilities, malware and attacks that target their mobile endpoints. Since joining the enterprise ecosystem, employee smartphones and tablets have fast become the weakest link in enterprise security. These current-day mobile computers have become the home for security risks. These risks exploit device OS vulnerabilities, malicious and malware-infested consumer apps, and the unsecured networks they connect to every day, just to name a few examples. Where does that leave your company’s attempts to secure all of the devices and apps in your network? Doesn’t feel very, well, secure does it?
Over 70 percent of enterprises recently admitted in a survey by Ponemon they believe they incurred a data breach because of insecure mobile devices. A recent scan by security firm Webroot of over 20 million apps from app stores reported that more than half were risky if not malicious.
Concerning? Extremely. Surprising? Hardly. Neither is the BYOD reality that you can’t fully protect data on devices that you don’t own. The myth of Achilles’ heel is real, and it lives in the smartphones, tablets and apps of your enterprise mobility program!
So how can your organization go out essentially in to battle against mobile threats day in, day out with greater security? Leave Achilles off of the battlefield! Corporate data is far too valuable and sensitive to leave inside your weakest endpoint.
It’s that motivation that helped us develop Virtual Mobile Infrastructure (VMI) – leave zero data on mobile devices. Keep apps remote where you have full control over your environment, and where you can reinforce and patch your network against vulnerabilities. Under VMI your apps are transferred as a display only to your employees’ devices, but a highly mobile-centric remote display protocol will make them feel as if they’re working with native apps on the device.
MDM (Mobile Device Management) or MAM (Mobile Application Management) approaches use multiple protocols (one for each app). VMI uses just one flat protocol, this greatly reduces attack points that hackers will no doubt try to breach.
It’s been great seeing the reaction of people working with the Nubo player live here at RSA, and seeing their reaction to the combinations of maximum security and native user experience that is available today.
Try Nubo out for yourself on your handheld and let us know what you think at info@nubosoftware.com!
Category: Mobile
As organizations continue to recognize the strategic value of mobile business processes and work towards enabling BYOD, they’re realizing the need to provide end users with secure access to enterprise apps that perform with the same speed and ease-of-use as the consumer apps they already engage with on their smartphones and tablets.
But integrating new mobile-first technologies with legacy systems made to solve yesterday’s challenges is exhaustive and expensive – so much so that legacy system operations and maintenance often account for more than half of enterprise IT budgets. These barriers can often delay and stagnate business growth, expansion, and well, progress!
So how do organizations feasibly move forward in this scenario? Small and medium-sized businesses with limited in-house IT capabilities often turn to Managed Service Providers (MSPs) to remotely manage their infrastructure and end-user systems. Larger organizations in both the private and public sectors consult with System Integrators to create and deploy custom apps and app stores for their mobile enterprise needs. But providing the type of security, that by design incorporates the nature of today’s mobile users and the apps they need to effectively add value, has been a work in progress.
Until now, the best solution available to integrators is one based on a device-centric EMM. This approach requires troubleshooting and diagnostic work in order to integrate customized architecture and apps with the client’s existing systems, hardware and communications infrastructure. This carries significant IT burden and still doesn’t eliminate all of the security and compatibility issues, the very issues that many organizations can no longer afford to deal with.
For example, physicians and other independent contractors working in healthcare often travel from one provider’s facilities to another. They need to connect to different apps provided by different providers – all on their one BYOD device. So what happens when one MDM solution is installed on their device and they then must work with apps provided by another company… which of course is using different security software? An IT headache, that’s what! A device can only be enrolled to one MDM server at a time, which makes it difficult to enforce one company’s security policies while still allowing employees to “BYOD” with others. There’s “only one sheriff allowed in town” as far as MDM security is concerned.
On the other hand, an enterprise mobility solution that can be easily implemented into current business processes and be instantly ready to use would be a boon to both integrators and their enterprise IT clients…
Enter Virtual Mobile Infrastructure (VMI). VMI removes the need to physically track and secure personally-owned devices. IT only has one virtual device that must be updated which runs in the data center. Under a VMI setup, there is no actual application running on the device, just a thin client. The apps are all run on a remote virtual platform, and the data management is not restricted to just one server. Apps can be distributed to multiple servers by simply switching the URL destination. This approach makes it easier for mobile professionals to switch seamlessly between different enterprise apps and platforms without their productivity being hampered by technical problems.
Lighten the load on IT for device management and app deployment
Managing devices has been a burdensome yet necessary headache for enterprise IT departments. They must find a way to keep track of all of the device versions floating around their BYOD network so that they can update them with the latest software and firmware to protect against new vulnerabilities. But the strain on time and resources extends beyond security. When it comes to app deployment, their often seeing double – managing both iOS and Android versions of the same app in order for it work effectively and securely for all of their employees.
VMI gives a completely separate virtual environment in which enterprise IT gains full ownership and control of the data. This allows both public and private sector projects to roll out the most current and robust consumer and business apps to their mobile employees. It also means they no longer have to compromise on user experience and can dip into the vast selection of preferred native mobile apps on the market. And those apps need only be integrated once to be compatible with both iOS and Android devices. Enterprises can deliver business-class native mobile apps to their end users without expending substantial time and resources towards trying to bridge integration and compatibility issues.
A true end-to-end business solution for system integrators
Integrators have been looking constantly for the ability to provide solutions that enable enterprise mobility, increase agility, save time and resources for IT, and provide the security without compromising the end user experience.
VMI enables the deployment of native mobile apps in a completely remote environment. System integrators can use VMI to deliver custom apps and app stores directly to their clients’ end users. In turn, their clients receive a true end-to-end solution that lets them distribute various apps to different teams and users as per their business needs. All of this can be accessed from the cloud, so accessing these tools is possible with almost no implementation time required.
Turning app deployment into a secure “Apps-as-a-Service” gives integrators a valuable solution to their clients. Enterprises can deliver business-class native mobile apps to their end users without expending substantial time and IT resources jostling with integration and compatibility issues.
The psychology behind why we enjoy interacting with different products has always played a huge factor in the degree to which we embrace or reject them. Long before the term was coined, user experience was always critical to differentiate your brand from your competitors. If a customer could not work (or play) with your product, if the functionality lacked intuition and made performing simple tasks perplexing, you’d already begun to lose them. Like spinach to a child or those nauseatingly dense textbooks you wanted to throw out your window in college, your product has become a chore, and if they can they’ll be content to avoid using it as much as possible.
Fast forward to our digital world and while the interface we interact with has changed that same psychology definitely applies. Whether it be for B2C or B2B, a web site or an app, accessed from a desktop, laptop, smartphone or tablet… users need to perform tasks quickly and easily, and even find the whole process relatively enjoyable. The consumerization of IT and rise of enterprise apps were a reaction to these realizations.
Mobile apps that incorporate the usability and UX best practices that have helped make consumer apps so popular are the ones that will be best adopted by employees. But they’re not the only ones who work more efficiently when given accessible and user-friendly tools…
Your IT admins need UX love too!
IT administrators often spend significant slices of their day managing user databases and enterprise app management. They’re the ones managing your BYOD operations day by day, adding and deleting users and devices, deploying selected apps and dispersing them amongst the relevant business units, and applying the latest patches and updates. Administering such tools is tedious and time-consuming, and takes valuable time resources away from more valuable projects.
You want to use an enterprise mobility solution that gives your IT clear, fast and efficient ways to complete administrative tasks. That requires a user-friendly interface, streamlined processes and reliable functionality that make managing your mobile network easy and boost productivity for everyone involved.
With Nubo’s control panel app, IT Administrators can BYOD too. They can access Nubo’s control panel and manage tasks effectively from their PC or laptop, smartphone, tablet or any HTML5 browser. The control panel app uses the same intuitive functionality and features as the remote workspace itself and all of the apps being delivered to employees.
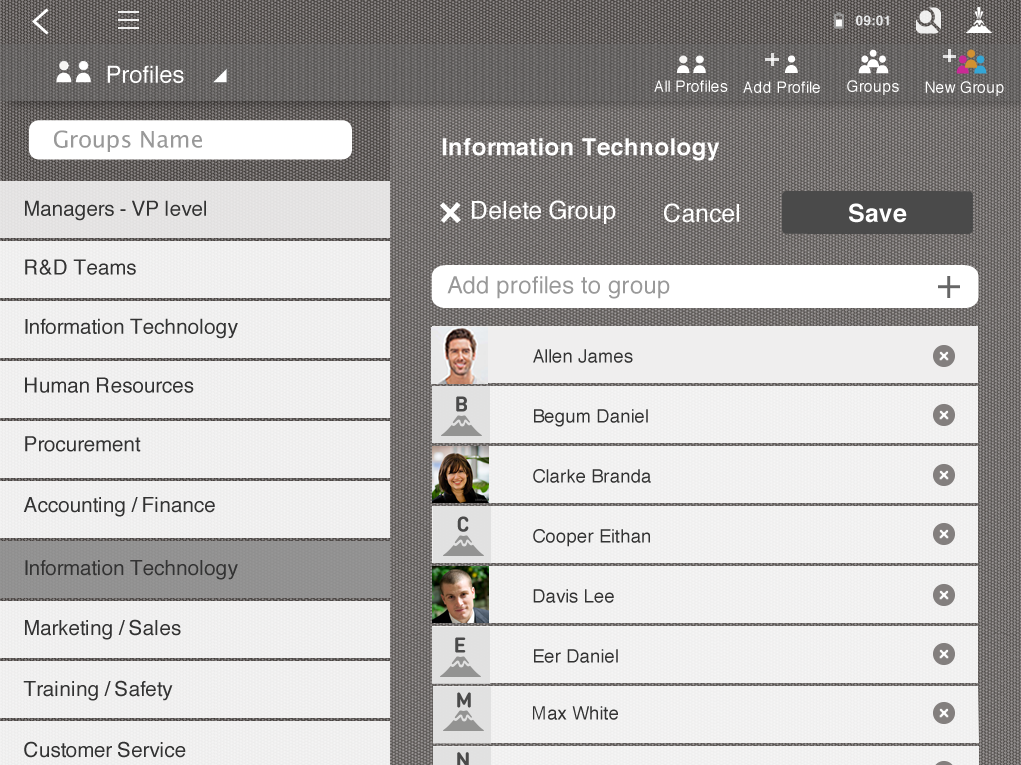
Admins can manage mobile end users and groups with ease using Nubo’s control panel.
Dragging and dropping APKs – An IT administrator’s dream
In a device-centric IT environment, apps must either be installed or downloaded to every user’s device. If you’re not installing your enterprise apps ad hoc to each employee, than you’re publishing that app to those users who then need to download it themselves. This makes tracking which users have actually installed the apps an adventure in babysitting, not to mention time-suckage.
With Nubo, admins can simply drag and drop an APK file from their directory to their corporate app store. From there, they can easily distribute the apps to individuals or customized groups. The app appears within the Nubo workspace for your selected employees. No registration or installation is needed, they can simply start working away with the app.
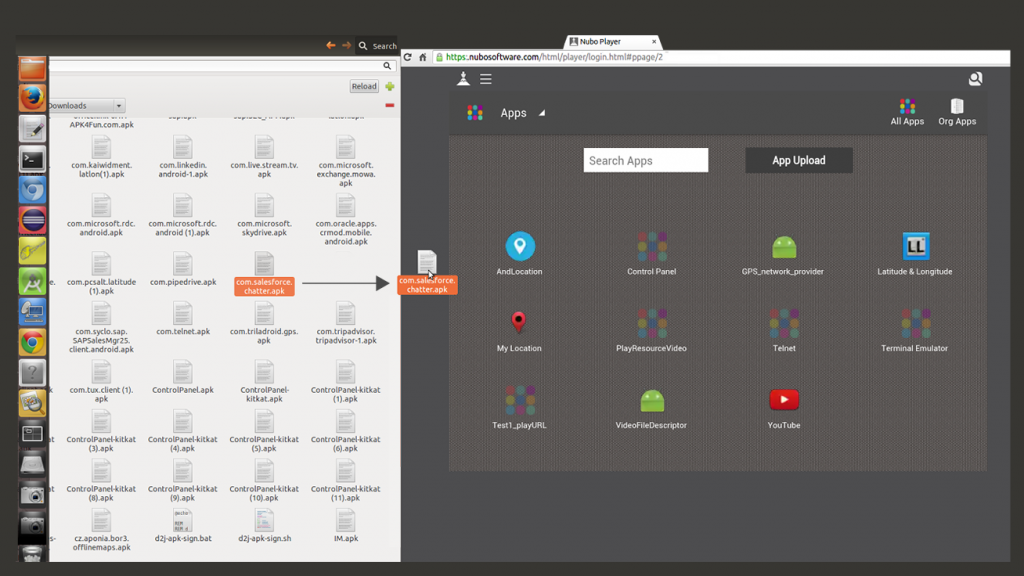
Installing apps to the remote work environment is as simple as drag and drop.
Give an IT administrator an easy, user-friendly control panel to manage all of these tasks and they’ll also become happy and productive end users!
Keeping corporate and personal worlds separate – A breath of fresh air
Having a robust remote platform to manage users and devices also gains IT confidence and provides a simplified process to deal with stolen or compromised devices. Admins can easily connect and disconnect devices from the network.
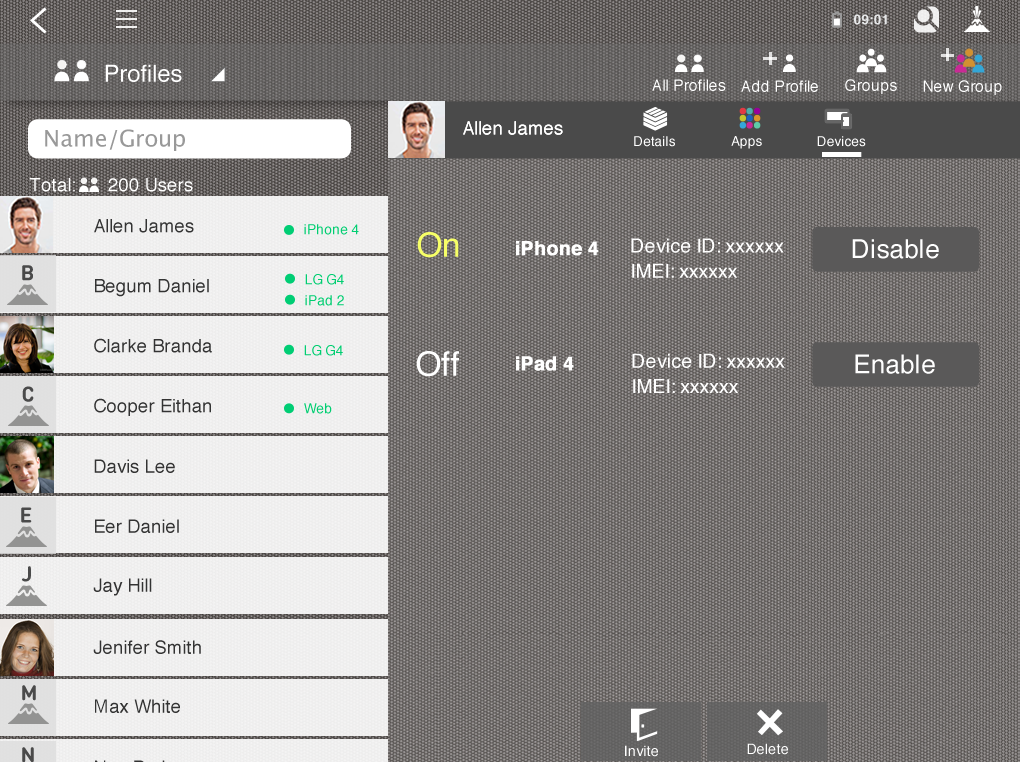
Devices can be connected or disconnected from the network with a click or a tap.
With the entire environment controlled remotely, IT can breathe easy knowing that no sensitive data has been jeopardized. They can also bid adieu to the larger BYOD headache caused by remote wiping employee devices.
More control, less stress and increased efficiency. Your IT administrators will thank you!












