

BYOD is no longer a trend – enterprises are already mobile, but it’s how they manage mobility and address roadblocks that will decide how successful they are going forward.
The largest barrier to mobile enablement? Security risks. From mobile malware, malicious apps, unsecured networks and software vulnerabilities to lost devices and Shadow IT, enterprises are learning that they can’t enforce enterprise-grade security on personal smartphones and tablets.
Still Managing Unmanaged Devices? You No Longer Need to with VMI
Consumer-owned mobile devices are the weakest link in enterprise security.Trying to manage the unmanageable, device-centric solutions have at best ‘contained’ the vast array of threats, but the results leave enterprises with a system that limits both mobility and security. Deploying complex, data-rich apps without compromise is the new standard, but MDM encryption will never mirror enterprise infrastructure. Device software vulnerabilities, sophisticated malware and malicious code will continue to evolve as attackers target lucrative proprietary and client data resting on devices. Stringent policies stifle your users, who can easily bypass device containers by jailbreaking or rooting their devices, downloading apps directly or using unapproved tools.
The solution? You can’t stop the constant proliferation of mobile security risks, but you can choose where to store your corporate data.
Stop ‘Containing‘ the Mobile Threat:
Take Back Your Corporate Data with Nubo Virtual Devices
Attackers can’t breach mobile data that isn’t there. Nubo Virtual Mobile Infrastructure (VMI) removes mobile devices from your enterprise security perimeter. Instead of managing physical devices, a virtual corporate device is streamed to your employees as a display only. leaving zero data footprint on their personal devices.
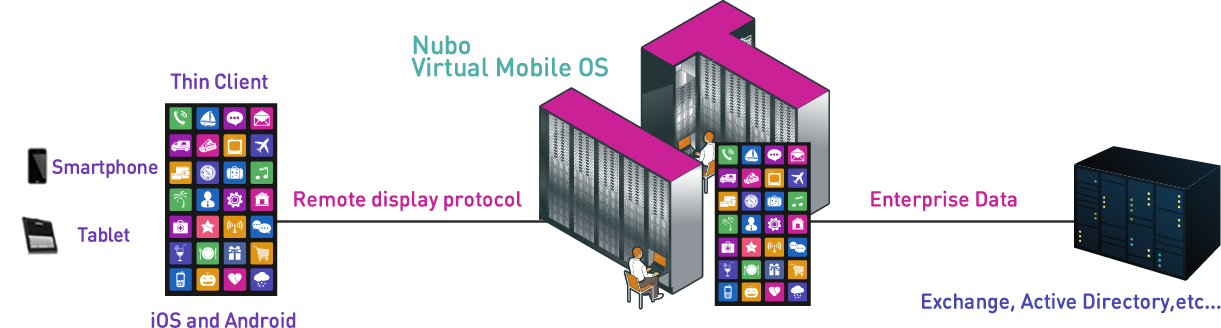
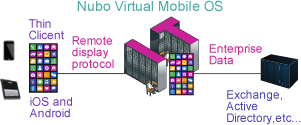
This entirely remote workspace is made possible by a mobile platform running on Nubo’s secured cloud infrastructure or your on-premises server. Your corporate virtual device is streamed to users as a display only via Nubo’s patented UX over IP protocol, which fully supports mobile sensors such as native touch, motion, GPS, orientation and camera.
Your users access their virtual workspace from any device with a thin client app available from the Google Play or App Store. Only display commands are transmitted from the server to the device to render data as a flat and non-analyzable image. Zero apps or data are stored on the device as they are merely a display for the user. Your employees may use any iOS, AndroidTM or HTML5-supported device, but you manage only one secure, remote workspace compatible with all of them.
Storing Your Data Where it’s Safest
Controlling all enterprise data remotely not only gives enterprises unmatched mobile security, it gives your enterprise full ownership of the OS. With server-level security, enterprise IT can now apply security updates that could never be possible on consumer devices.
Organizations can shift IT resources away from device management and towards enabling employees with the apps that matter most to their business. Employees can use their preferred smartphone or tablet to work on their remote virtual device. And still, all the data is located in your own enterprise organization data center.
Who Relies on VMI Security?
Defense, public safety, government, healthcare, banking and legal. Organizations managing the most sensitive data trust VMI technology for unprecedented data security and guaranteed compliance.
Learn more >
In-Depth Security Capabilities
Enterprises leverage Nubo VMI to reap the security benefits of a better design:
One Flat Protocol
Since the Nubo thin client app is merely a reflection of the apps running on the server, only one flat protocol needs to be transferred back to the data center. This avoids many of the typical security threats which attack VPN tunnels. Storing data on the device leaves other solutions no choice but to add an additional tunnel for each and every app installed. More tunnels mean more weak links for malware and hackers to attack. With Nubo, just one secured tunnel is needed no matter how many apps your employees require, facilitating mobile security scalability for your BYOD program now and in the future.
Inherently Secure
Nubo’s cloud SaaS service effectively separates personal devices from enterprise data. Unlike other BYOD solutions which store data on the device, the Nubo player acts only as a display. The user cannot transfer data to their device. This makes dealing with compromised devices stress-free and simple. When a device is lost/stolen or employees leave the organization, remote wiping is unnecessary and IT can simply block the user’s access.
Two Factor Authentication
Nubo combines its identification process with an authentication method that initially matches a user/password with the organization’s active directory and then sets up a password which the user enters each time they login. This achieves a complete and secured Two Factor Authentication process.
User Sandbox
Every Nubo user occupies a separate, protected sandbox within the virtual machine. Furthermore, every authorized app is isolated from other apps within the user sandbox. Each user’s personal data is stored separately and assigned individually to each user and app, which is also encrypted separately. Nubo uses several security measures, including SELinux and encryption to maximize sandbox protection.
Activation & Approval
Nubo turns an employee’s device into an item that safely validates the identification of a remote user. The first time that the Nubo app starts, it sends an activation request containing the user’s email address along with specific physical and operating system details that identify the device. This information is not stored on the device and is dynamically calculated every time the player is running. An activation key is then generated from 384 bit of cryptographically strong psuedo-random data that can only be validated against the original device. User validation and approval can then be obtained by receiving an activation email or having their device physically cleared and approved by their security officer.
Central Management for SSO and OTP Processes
VMI architecture lets you manage SSO and password management from a much more controlled environment. A reflected image of the apps is transferred to devices using remote display protocol. OTP systems and all other authentication details are not exposed to mobile devices, neutralizing many of the security risks that mobile devices have introduced to your network.
NSA Suite B Secure Communication
All communication between the devices and the Nubo platform is encrypted via TLS 1.2 and with the strongest encryption algorithms specified by NSA Suite B, ensuring that it is secure even if the user is using public or even unsecure WiFi networks. The Nubo client validates the identity of the server and verifies that your users will only connect to your enterprise server.










 Download our Security White Paper to dive deeper into Nubo VMI.
Download our Security White Paper to dive deeper into Nubo VMI.